Finally, as promised, I will talk about the "Hello Pervert" scam email, but first I have to thank @EwanDoggieNG (sorry if I keep pestering you by mentioning you^^') because he was the one who told me about this scam under the comment section of another important scam I talked about that is more common but not less annoying nor fright-inducing the so-called "I have accidentally reported you" scam. The "Hello pervert" scam is a type of sextortion email where scammers claim to have compromising videos of the recipient and threaten to share them unless a ransom is paid.
The fear and the spoofing
The two core elements of this type of scam is fear and spoofing, more specifically email spoofing. What is spoofing? Spoofing is a type of attack in which a person or program successfully identifies as another by falsifying data, to gain an illegitimate advantage.
what is the goal of spoofing? The goal is to steal data or money, or gain unauthorized access to systems. It can be thought as a short-term form of identity theft. Scammers typically keep their impersonations brief, manipulating an email, text message, phone call, or website to pretend to be a friend, company, government entity, or other reputable source.
Is it always malicious? No, spoofing does also have legitimate uses, such as in cybersecurity testing, or as a form of privacy protection where individuals want to mask their identity or activity. But the regular user who receives a spoofed message/call/email etc. should be wary of it as it's more likely they are a target of such attack.
Types of spoofing:
- email spoofing
- DNS spoofing
- Caller ID spoofing
- Text spoofing
- Website spoofing
- IP spoofing
- Filename extension spoofing
- Facial spoofing
- MAC spoofing
- GPS spoofing
- ARP spoofing
If you want to know more about these types this link mentions them: https://us.norton.com/blog/online-scams/what-is-spoofing#id-toc-12-different-types-of-spoofing-with-real-life-examples-2
When used as illegal tool, spoofing can be quite dangerous because if someone spoofs your details, attackers may impersonate you to deceive others, potentially leading to fraudulent activities carried out under your name. It's a form of identity theft with long-term legal and reputational damage and can be also quite hard to prevent.
What matters to us now, for the purposes of this blog, is email spoofing which is part of this scam, but before seeing it a quick technical aspect of sending emails.
When electronic mail transmission occurs a protocol is used: Simple Mail Transfer Protocol (SMTP)
Simple Mail Transfer Protocol
What is it? It is an Internet standard communication protocol for electronic mail transmission. Mail servers and other message transfer agents use SMTP to send and receive mail messages. User-level email clients typically use SMTP only for sending messages to a mail server for relaying, and typically submit outgoing email to the mail server on port 465 or 587 per Request for Comments (RFC) 8314. Email is submitted by a mail client (mail user agent, MUA) to a mail server (mail submission agent, MSA) using SMTP on Transmission Control Protocol (TCP) port 465 or 587. Most mailbox providers still allow submission on traditional port 25. The MSA delivers the mail to its mail transfer agent (MTA). Keep in mind that SMTP defines message transport, not the message content. Thus, it defines the mail envelope and its parameters, such as the envelope sender, but not the header (except trace information) nor the body of the message itself (1). Basically this protocol operates by sending lines of text back and forth between the client and the server. The client sends commands and eventually the email message, and the server sends back responses to tell the client if the server accepted the command or if something went wrong.
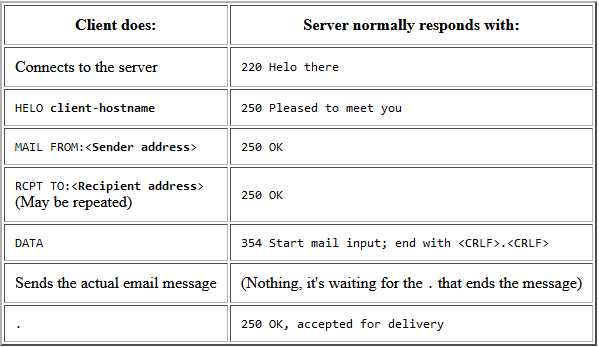
SMTP conversation between the client and the server. Do you see those three digits (i.e. 250)? They are a special format made of three digits, a space (or a dash), and then some free-format text (in error messages, this is usually intended for users to read; otherwise it is generally just noise). The real important thing to pay attention when it comes to response it's the first digit:

So in the example above you see 250, that 2 means that there are no problems or errors.
So when a SMTP email is sent, the initial connection provides two pieces of address information called the "envelope" addressing which are:
- MAIL FROM: it is generally presented to the recipient as the Return-path: header but not normally visible to the end user, and by default no checks are done that the sending system is authorized to send on behalf of that address
- RCPT TO: it specifies which email address the email is delivered to, and again it is not normally visible to the end user but may be present in the headers as part of the "Received:" header
Unless there are problems signaled by the receiving mail server, the sending system sends the "DATA" command, and typically sends several header items, including:
- From: an example is johnsmith-@-exampleemail.com, as always the address visible to the recipient, but again, by default no checks are done that the sending system is authorized to send on behalf of that address
- Reply-to: example joesmith-@-anotherexample.com, just like "from" no checks are done
- Sender: example xuxing-@-totallynotchineseemail.com similar to "from" and "sender"
The result is that the email recipient sees the email as having come from the address in the From: header. They may sometimes be able to find the MAIL FROM address, and if they reply to the email, it will go to either the address presented in the From: or Reply-to: header, but none of these addresses are typically reliable, because automated bounce messages may generate backscatter (incorrectly automated bounce messages sent by mail servers, typically as a side effect of incoming spam) (2).
How boring, tell us the spicy stuff!
So how does email spoofing works? It usually works by altering the header information of an email to make it appear as if it is coming from a trusted source. Attackers manipulate fields like the "From" and "Reply-To" addresses, tricking recipients into believing the email is legitimate, which can lead to phishing or other malicious activities. This is why I wanted to talk about the technical aspects because now you can better understand some words used in the next part where I'll talk about the scam itself. So the spoofer creates a fake email address designed to mimic that of a real person or a trusted institution. The attacker then alters email header metadata like the sender’s address and subject line, crafts their message, and sends the spoofed email to their target.
A bogus email address that closely resembles that of the person or organization they’re impersonating is created by the criminal (remember it's a short-term identity theft), then the attacker modifies the email's header information—such as the "From," "Reply-To," and "Sender" fields—to make it look like the email came from a trusted source. This bogus message is crafted to dupe the recipient into believing the email is legitimate and engaging with the scam. Finally the spoofed email is sent and if it’s convincing enough, the target may be tricked into clicking a malicious link or providing their personal details.
So now that you have an overall, very simplistic knowledge of what's behind a spoofed email, let's dive into the "Hello Pervert" scam itself.
"Hello pervert" scam
As I said at the beginning of this blog, this scam is a type of sextortion.
What is sextortion?
It's a non-physical forms of coercion to extort sexual favors from the victim. Sextortion refers to the broad category of sexual exploitation in which abuse of power is the means of coercion, as well as to the category of sexual exploitation in which threatened release of sexual images or information is the means of coercion. In the most common type after obtaining naked photographs or videos of the victim, the scammer then threatens the publication of these pictures or to send them to close friends and family members. A demand of money is then made, though usually the scam is either a bluff (e.g. the scammer never intended to publish them) or the pictures/videos are published regardless even if the money is sent. It's also a form of blackmail in which sexual information or images are used to extort money or sexual favors from the victim. Social media and text messages are often the source of the sexual material and the threatened means of sharing it with others.
fun fact: an early use of the term appears in print in 1950 in California in "Sextortion Charges To Come Up Next Week". Los Angeles Times. April 5, 1950.
For more info about it, here a link: https://cyberbullying.org/sextortion
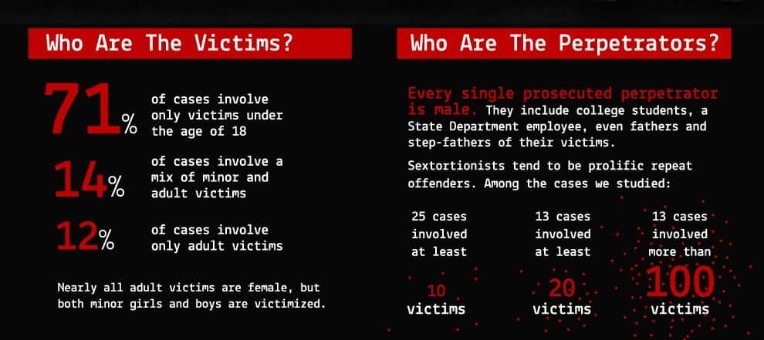
from: https://www.comparitech.com/blog/information-security/what-is-sextortion-examples/
How does this scam works?
The emails claim that the sender has been watching your online behavior and caught you red-handed doing activities that you would like to keep private. The email usually starts with “Hello pervert” and then goes on to claim that you have been watching porn. The sender often says they have footage of what you were watching and what you were doing while watching it. I post here two variants of this scam:
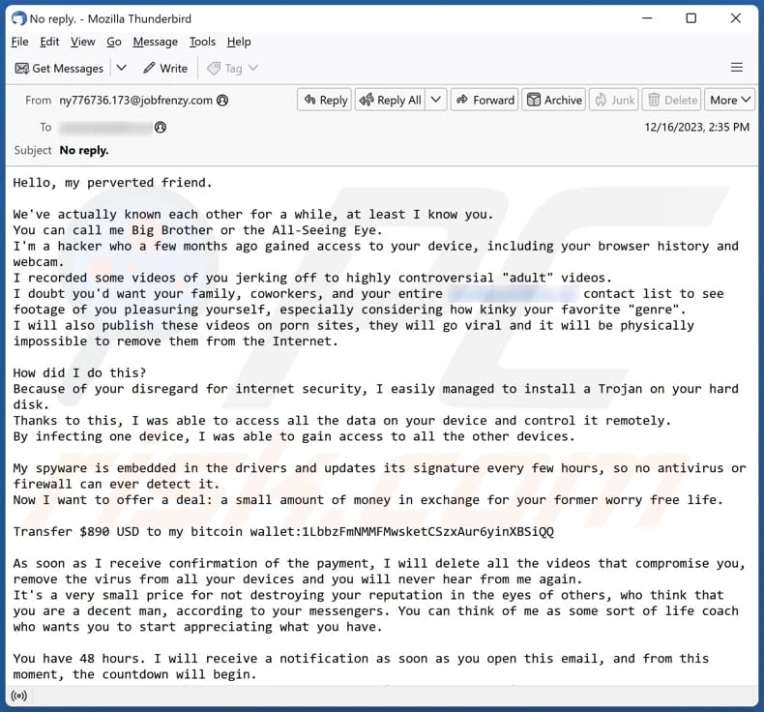
from: https://www.pcrisk.com/removal-guides/28629-hello-my-perverted-friend-email-scam
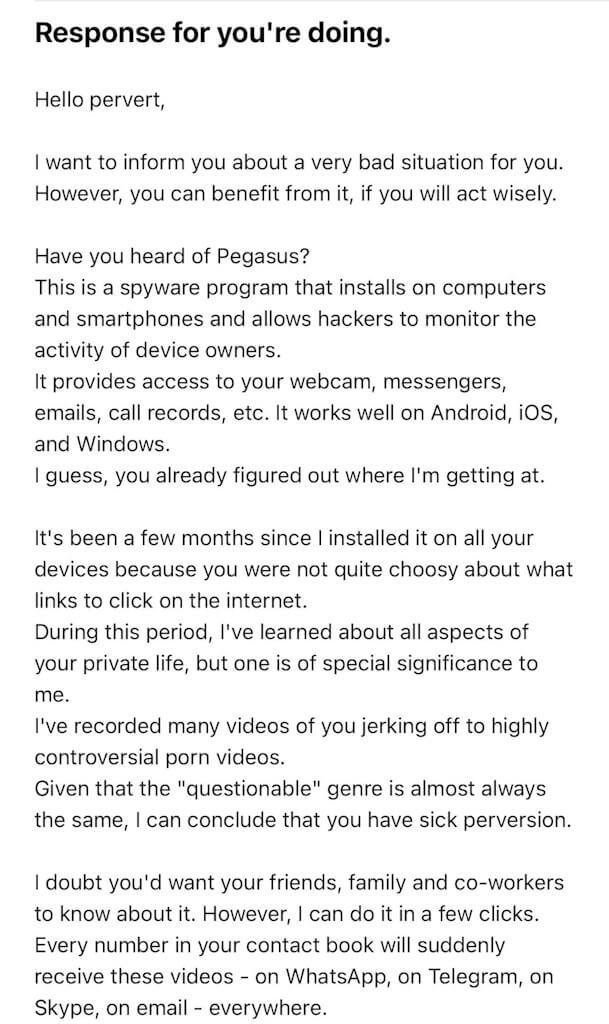
from: https://macsecurity.net/view/625-hello-pervert-scam-email-what-is-it-and-how-to-stay-safe
So as you have noticed, the email usually starts with “Hello pervert” and then goes on to claim that you have been watching porn. The sender often says they have footage of what you were watching and what you were doing while watching it and have installed Pegasus an infamous multi-platform spyware created by the NSO Group based in Israel.
FIRST LIE: PEGASUS
Pegasus is designed to be covertly and remotely installed on mobile phones running iOS and Android, meaning it runs on mobile while the e-mail mentions computers and that's not true. The attacker takes advantage of informatic science illiteracy of the victim to scare them to death and make them more compliant to the "hacker's" request. While NSO Group markets Pegasus as a product for fighting crime and terrorism, governments around the world have routinely used the spyware to surveil journalists, lawyers, political dissidents, and human rights activists; Italy knows this very well since several journalists and NGO people had their phones hacked by this.
The spyware can be installed on devices running certain versions of iOS—Apple's mobile operating system—as well as some Android devices. Rather than being a specific exploit, Pegasus is a suite of exploits that uses many vulnerabilities in the system. Infection vectors include clicking links, the Photos app, the Apple Music app, and iMessage. Some of the exploits Pegasus uses are zero-click — that is, they can run without any interaction from the victim. Once installed, Pegasus has been reported to be able to run arbitrary code, extract contacts, call logs, messages, photos, web browsing history, settings, as well as gather information from apps including but not limited to communications apps iMessage, Gmail, Viber, Facebook, WhatsApp, Telegram, and Skype.
Pegasus hides itself as far as is possible and self-destructs in an attempt to eliminate evidence if unable to communicate with its command-and-control server for more than 60 days, or if on the wrong device. Pegasus can also self-destruct on command. If it is not possible to compromise a target device by simpler means, Pegasus can be installed by setting up a wireless transceiver near a target device, or by gaining physical access to the device (3).
Despite sadly no one is safe from this damn spyware, it's usually used for high-risk targets, such as political activists, government officials, and journalists, and chances a lamer like the person who's trying to steal your money infected your devices (even computers despite the spyware does not infect computers!), are zero. There is essentially no proof that such a closely-guarded spyware has ended up in the hands of everyday scammers.
Common traits of this scam:
- threats and fear-mongering words: the email goes on to claim that embarrassing videos have been recorded through the victim’s webcam, threatening to send the videos to all of the victim’s contacts unless a ransom payment is made. The message creates a sense of urgency, giving a deadline of usually 48 hours to pay the ransom before the videos are distributed.
- demand of payment: a payment is demanded in the form of untraceable cryptocurrency, such as Bitcoin or Litecoin. The email provides a specific cryptocurrency wallet address where the funds should be sent. amount of money demanded varies, but is often between $500-$1000 even if I've recently seen prices even higher (+$1,600), probably because they want to test how much a victim is willing to pay for the data to stay private
- reassurance of video deletion: the attacker promises that if the ransom is paid in full by the deadline, the videos will be permanently deleted and the malware removed from the victim’s devices. There is no guarantee images will be deleted after payment nor they have already been sent.
A new strain and an old tactic: images of your location and old passwords
Just like a fucking virus which evolves fast due to high mutation rates, the large population sizes, short generation times, the lack of proofreading mechanisms inherent in their polymerases (specifically for RNA viruses) and high mutation rates, so this scam evolves rapidly to give a more sense of reliability and truthfulness. Adding the photo of your location gives a more reliable layer to the scam but how did it happen? From data breaches; when scammers have access to such data, it may also include your physical address. With that knowledge, scammers have increased their threats by simply adding a photograph of your personal neighborhood by looking it up online. For most places in inhabited areas, you can grab such pictures from Google Maps or similar apps. This reddit post shows it despite it has been deleted, basically the scammer used an old PO box address. But it’s true that this adds a convincing argument to the claim that the sender has been spying on you:
https://www.reddit.com/r/Scams/comments/1f6gki0/deleted_by_user/
So keep always in mind that popular scam that is doing the rounds right now involves old passwords. These passwords may have been involved in data breaches years ago, so chances are that victims don’t even use them anymore. However, seeing your old password in an email could be enough to make you wonder if the sender does indeed have anything compromising. Fraudsters claim to have intimate images or videos and threaten to share them with contacts or post them online, although they are often bluffing and have nothing to reveal. It's a very profitable tactic.
How did the scammer obtain the old password? It's very likely that the scammers bought your password from other cybercriminals that obtained them during one of the countless data breaches that hit company after company every week.
As an extra threat the email may include something like:
“Or is visiting [your physical address] a more convenient way to contact if you don’t take action. Nice location btw.”
Implying that they know where you live and threatening to stop by and create a scene. Again don't fall for it, don't let fear take over your mind.
What do to if you receive this email?
Disclaimer: once again I will use caps locks, because you must carve this into your minds!
1) DON'T PANICK! IT'S A FUCKING SCAM!
2) DON'T OPEN UNSOLICITED ATTACHMENTS! NEVER!!! AND I REPEAT NEVER!
3) HOW DO I VERIFY IT? BY CHECKING THE EMAIL HEADER. HOW???? CONTROL EMAIL-AUTHENTICATION RESULTS!
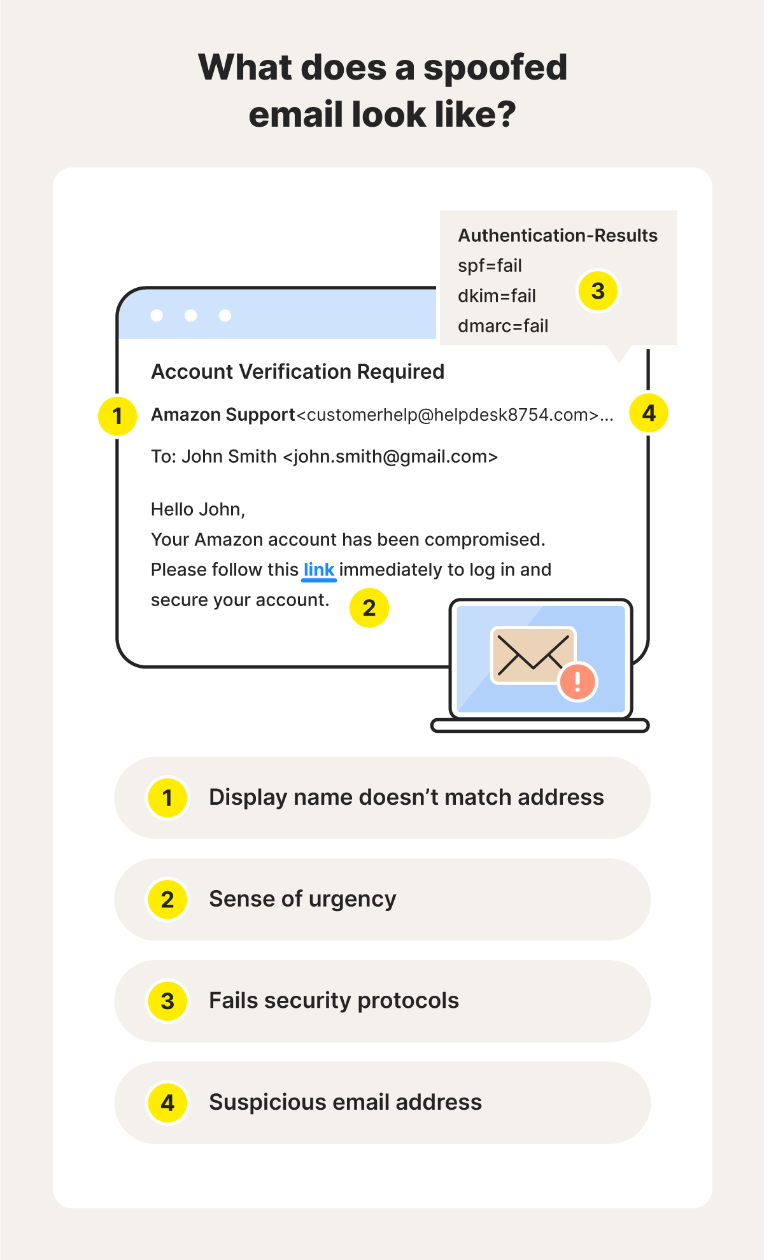
from: https://us.norton.com/blog/online-scams/email-spoofing
4) WTF ARE SPF, DKIM, DMARC????? ARE THEY CODE NAMES? NO! THOSE ARE THE EMAIL AUTHENTICATION HEADERS! THEY ARE YOUR BEST FRIENDS AT DETECTING THE VALIDITY OF AN EMAIL. KEEP THEM CLOSER TO YOUR HEART!
If you look at the raw email, sometimes called “source” or “original”, you can see more information about the email and how it got to you. Specifically, you want to look for headers that indicate the authentication status of the email message. consists of:
- SPF
- DKIM
- DMARC
By implementing email authentication, you can ensure that anyone — an employee, customer, partner, or prospect — who receives an email that purports to be from your company can determine if the email is legitimate and, if not, flag or discard it.
Can you explain me like I'm five?
Yes, SPF stands for Sender Policy Framework and answers the question "does the server sending this have the right to use the domain name, or names, listed in the message’s headers?" Basically SPF allows domain owners to decide which IPs can send emails on behalf of their domain. The email will only be delivered if a server matches one of the SPF’s allowed IP addresses.
DKIM stands for DomainKeys Identified Mail and answer the question "if there’s a cryptographic signature attached to the message, does it match the public key on file for the domain it appears to be from?" DKIM uses key cryptography to sign an email message and this signature verifies that your message came from the right domain and wasn’t altered during the sending process.
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance and answers the question "do the headers match one another?" For instance, are the From: and Reply-to: fields the same? If a domain is at DMARC enforcement, the domain in the From: field can be verified by the receiving domain, meaning that you can trust that the person who is sending that email is actually the right person. If the email is not authorized, the DMARC policy will reject or quarantine the message. Basically this email authentication policy and reporting protocol builds on and incorporates the previous two (SPF and DKIM).
Awwww, thank you, but now how the fuck do I see these????
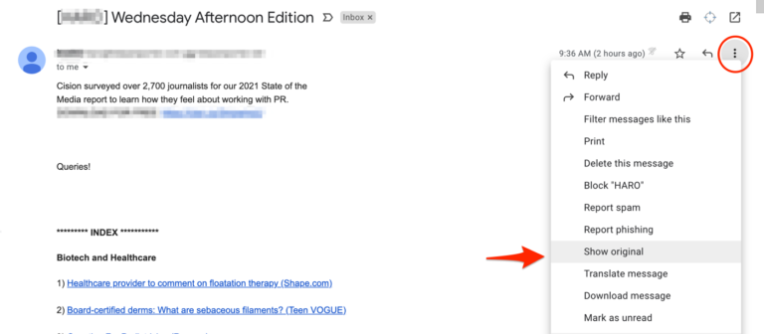
Well, the email headers can be found in a variety of ways, depending on your email application. If you use Gmail:
1) open the email message in Gmail, then select the More menu to display additional options
2) select Show original from the menu
3) Gmail opens a new tab that shows the full message
4) you will see the headers that indicate the authentication status of the email message which are:
4a) SPF
4b) DKIM
4c) DMARC
BUT SPF and DKIM are not sufficient to truly check the validity of the email, the acid test is DMARC. For an email to pass DMARC, it must pass either SPF or DKIM with an aligned identifier. What this typically means is that the domain used for the SPF or DKIM check and the domain publishing the DMARC policy must at least be part of the same DNS namespace. The results are pass/fail.
from: https://blog.cloudhq.net/what-is-metadata-and-how-do-you-find-email-metadata/
In the link provided above you will find how-to for other main web email providers. If you are using Tuta, go to the three dots of the opened email, click on them, then "Show email headers":
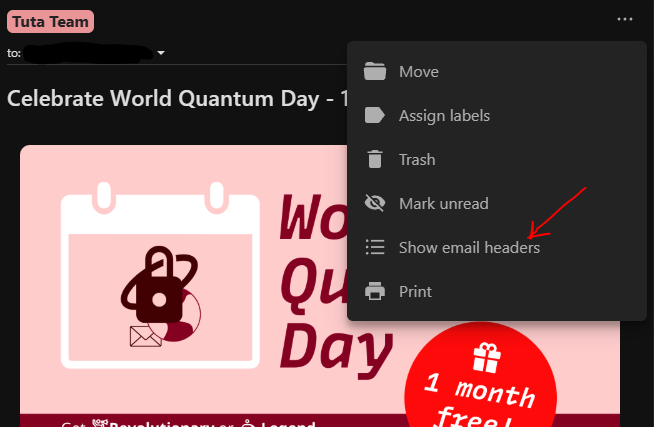
Authentication results:
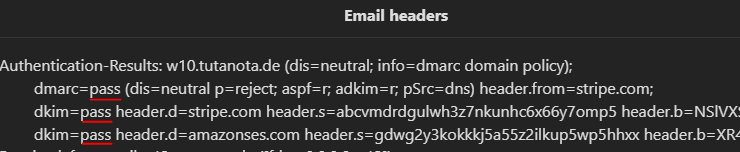
The email is legit and valid. While this is the authentication results for the "Hello pervert" email:
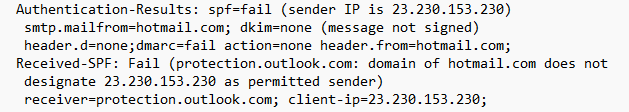
I suggest you to read it as it also talks about the encoding errors that show how the scammer riddles with encoding errors the email, which typically appear when Cyrillic or other non-Latin characters are misinterpreted as UTF-8 or quoted-printable, or when text is generated or processed by automated systems not properly handling character sets.
5) DON'T INTERACT WITH THE ATTACKER! THIS WILL SIGNAL THAT YOUR EMAIL IS ACTIVE AND WILL MAKE IT A TARGET FOR FUTURE AND MORE PHISING/SCAMMING/SPOOFING ATTACKS!
6) REPORT TO AUTHORITIES, BECAUSE THE MORE THEY GET IT, THE MORE TOOLS THEY MAY HAVE TO COUNTERATTACK THEM
7) BLOCK THE SENDER, THROW IN THE BIN THE MESSAGE AND SLEEP SERENE DREAMS
Well, I think that's all for now. I really wanted to cover as much as possible using all the sources that helped me to gain more knowledge on how to better protect me. Stay safe and always check the email headers, even for normal emails. This way you will train your mind to be more wary of everything that arrives in your inbox because billions of spoofed emails are sent every fucking day. Have a nice day and take care!
Last but not least just to laugh a bit: reply to a hello pervert email only if it comes from your boyfriend, girlfriend, husband or wife like someone on Reddit said XD
EDIT: I added "-" to those email examples to avoid making people think those are legitimate email addresses. Those are just example.
References and footnotes:
https://us.norton.com/blog/online-scams/what-is-spoofing
https://www.rfc-editor.org/rfc/rfc8314
(1) https://web.archive.org/web/20190403055256/http://utcc.utoronto.ca/usg/technotes/smtp-intro.html
(2) https://slate.com/technology/2002/03/e-mail-impersonator.html
Blackan
Pretty informative on this
I had this scam email before but I didn't do anything with it and just ignored it and deleted it,definitely felt like a scam
Definitely living in a scary time with the rise of doxxing and leaks occuring as often
Your doing the world a favour informing the community on this
ShangXian
Interesting. You did the right and only thing to do when encountering this scam: do nothing, report, block and ignore. Did the scammer mention Pegasus? Before it, they usually mentioned Trojans but they never explicitly said the name to stay as generic as possible to avoid a tech-savy might catch them red-handed.
And now with AI, machine learning and deepfakes (both visual and acoustic) this scam can become more scary, because they can fabricate videos of you while having fun with yourself. But again the strategy is doing what you did, never interact with them and check the email authentication headers.
Thanks, glad you liked my blog^^ have a nice day!